Working with SAS tokens
SAS tokens are secure access tokens that provide delegated access to resources on your storage account. The storage service confirms the SAS token is valid in order to grant access. The construct of a SAS token includes the permissions granted on the token, the date validity, and the signing key for the storage account. When creating a SAS token, several items need to be considered that govern the granular level of access granted, which are as follows:
• Resource types that the client might use
• Permissions on the resource types that are required
• The period the SAS key should function for
Types of SAS
There are three types of SAS supported by Azure Storage:
• User-delegated SAS: This is aSAS token that is secured by AD credentials.
• Account SAS: An account SAS is created and secured using a storage key. The permissions granted can span several services (blob, file, queue, and table), as well as accessing permissions for the chosen services.
• Service SAS: A service SAS is identical to an account SAS except that it is limited to a single service. There are limitations to some read, write, and delete operations for a service SAS that the account SAS has higher privileges to allow.
Forms of SAS
SAS tokens can take two forms, as detailed here:
• Ad hoc SAS: This SAS token is created as needed where permissions are chosen along with accessible services in alignment with the type of SAS used. The configuration is specified in the SAS URI. This is generally used for scenarios where quick access is required for a temporary period. SAS tokens cannot be managed after being issued. User-delegated SAS and account SAS can only be provisioned as an ad hoc SAS.
• Service SAS with stored access policy: This form of SAS token is more secure and enhances the functionality that an ad hoc SAS token delivers. SAS tokens can be managed after being issued and are manufactured to comply with policies configured in the stored access policy. SAS tokens can be modified and deleted using a stored access policy.
Top Tip
Microsoft advises a best security practice is to use Azure AD credentials whenever possible.
Now that you have an understanding of the core components of a SAS, we will explore some exercises for creating and managing these.
Generating SAS tokens
In this demonstration, you will learn how to create a SAS token for sharing access to a storage account:
- Navigate to the Azure portal by opening https://portal.azure.com.
- Go to a storage account.
- On the left menu for the storage account, clickShared access signature under the Security + networking context. Create a new SAS key by selecting the Container and Service options on the Allowed resource types options list. Change the Allowed services option list as desired.
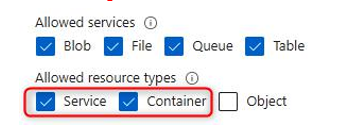
Figure 7.16 – SAS permissions
- Set the time for start to 5 minutes from your current time and click Generate SAS and connection string. Copy the connection string – you are only ever presented with this once.
- Open Azure Storage Explorer, then click the Open Connect Dialog button.

Figure 7.17 – Open Connect Dialog
- Click Storage account or service, and select Connection string as your connection method, then click Next.
- Paste the connection string copied earlier into the Connection string dialog. Change the desired Display name text if desired. Click Next.
- You will be presented with a summary page noting all endpoints and other details. Click Connect.
- You will get a success message as follows:
Figure 7.18 – Storage Explorer – Success message
- Navigate through the hamburger menu to the Storage Accounts section, click the arrow to open all accounts, and notice your storage account connection.
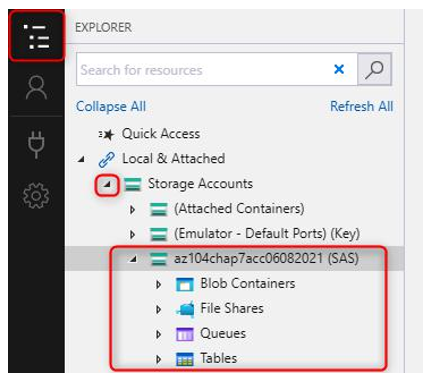
Figure 7.19 – Storage Accounts
You now know how to generate a SAS token and connect to a storage account using the token. In the next section, we will explore storage access policies and how these enhance the concept of SAS tokens.
Top Tip
Allowed protocols should be limited to HTTPS on the SAS creation for enhanced security. The SAS start and end time should be limited as far as possible to the necessary time required for access.